Appearance
Enabling and Verifying SSL/TLS Encryption
The Yellowbrick server supports SSL/TLS encryption for client communications and passwords, including remote connections to the SMC and connections via client tools and applications.
Connection Prerequisites
TLS/SSL version 1.2 is required, as provided by openssl version 1.0.2 and later, which exists on almost all current operating systems. To check your version on Linux/UNIX, macOS, and Windows platforms, run the openssl version command. For example:
$ openssl version
OpenSSL 1.0.2g-fips 1 Mar 2016SSL-Only Mode
If you want to automatically enforce SSL mode for all client connections, you can set the cluster to SSL-only mode. When the cluster is running in this mode, all client connections from all tools, including connections to the SMC, the front-end PostgreSQL database, and ybtools, must connect via HTTPS. All non-SSL connections are rejected.
Enable SSL-Only Mode and Import Certificates
Follow these steps to enable SSL-only mode in the SMC. If necessary, you can import certificates as part of this procedure.
The initial SSL certificate for a Yellowbrick database is established with a self-signed, untrusted SSL certificate. Your organization may choose to change this database certificate to align with its internal policies by importing a certificate signed with a private signing authority/CA or by using an external signing authority. Without a Certificate Authority (CA)-signed certificate, you may get errors such as:
There is a problem with this website's security certificate.The Import Certificate button in the SMC allows customers to import a new SSL certificate for the database. The same certificate is used for establishing trust to both the HTTPS listener and the Postgres TLS listener. The import must be done with a PEM-encoded certificate issued by a third-party CA or a custom CA trusted by the organization's standard browser.
To enable SSL-only mode:
- Log into the SMC as the
yellowbrickuser. - Go to Configure > Settings > SSL.
- To import a new certificate, click Import Certificate and import the public key and the private key. You must specify the password for the private key. Be prepared to provide all three values: both keys and the private key password.
Although the format of the files being imported is text, it is encoded as follows:
-- BEGIN PRIVATE KEY -- <data> -- END PRIVATE KEY
...
-- BEGIN CERTIFICATE -- <data> -- END CERTIFICATE KEY --- Select the Enable SSL-only communications checkbox. (Skip this step if you only want to import a new certificate.)
- If required by your certificate, enter a fully-qualified hostname for the SMC in the Automatic Redirect field. Redirection is commonly used to match the Common Name (CN) or Subject Alternative Name (SAN) in an SSL certificate to the URL a user visits in order to establish trust. If browsers attempt to log into the SMC via an HTTP URL, those connections will be redirected to the hostname you entered, using HTTPS.
For example:
http://yb100will be redirected to:
https://yb100.redirectme.comassuming you entered yb100.redirectme.com in the Automatic Redirect field.
- Click Save Settings in the top-right corner of the Configuration Settings screen.
- Restart the database as prompted, using
ybcli:
$ ybcli -y database stop
...
$ybcli database startVerifying That Connections Are Secure
You can verify that a session is using a secure SSL connection in two ways:
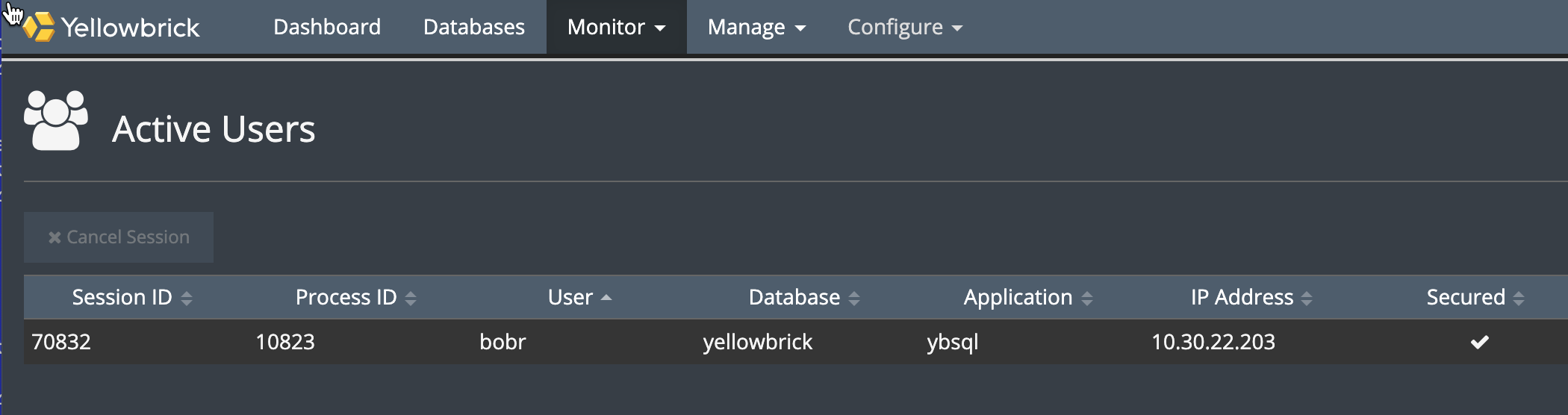
- Check the SMC. Go to Monitor > Active Users and note the Secured column. For example:
- Query the sys.session view. For example, the following query returns information for the current session user, showing that the connection is secure:
yellowbrick=> select su.name, ss.session_id, ss.client_ip_address as client_ip, ss.user_id, ss.secure_connection as secure, ss.secure_details
from sys.session ss join sys.user su on ss.user_id=su.user_id
where su.name=session_user;
name | session_id | client_ip | user_id | secure | secure_details
------+------------+-----------------+---------+--------+----------------------------------------------
bobr | 70832 | 10.30.22.203/32 | 16397 | t | TLSv1.2/ECDHE-RSA-AES256-GCM-SHA384/256 bits
(1 row)Parent topic:Configuring SSL/TLS for Tools and Drivers