Appearance
Users and Roles
This section describes the types of users and roles that exist, and can be created, for Yellowbrick Data Warehouse cloud deployments. Administrator accounts can be set up at multiple levels, based on a set of predefined admin roles. Database user accounts can be set up with or without access to Yellowbrick Manager. Database users and roles exist separately per data warehouse instance. Different sets of users and roles may belong to each instance in the same cloud deployment.
The following users and roles are created by CDWM when a new VPC is deployed.
- ybdadmin@realm (initial login user)
A new Yellowbrick cloud deployment creates a
ybdadmin@*****.comlogin for administration, using the domain (realm) for your VPC. The password provided for this account must be changed on first login. This account is intended for initial login to Yellowbrick Manager, but is not intended for extensive use. Theybdadminuser will be invited to create the first data warehouse instance and will become its owner. After that, theybdadminuser should create new users and roles with the same privileges or fewer privileges, as required.ybdadminis a member of all other predefinedadminroles (and a member of the consumer role):clusteradmin- consumeradmin
- instanceadmin
securityadmin: privileges to create, drop, and alter roles and users, as well as external authorization controlsysadmin: broad privileges at the system, session, and database level, but no privileges on clustersuseradmin: privileges to create, drop, and alter roles and users
- clusteradmin role
This role grants all privileges on clusters, including the ability to create new clusters, and alter, drop, or use any cluster for a given instance.
- consumeradmin role
This role is designed for administrators of a specific Yellowbrick cloud deployment. This role confers privileges to create and manage instances, run diagnostics, and perform upgrades. In other words, this role has privileges for a specific VPC deployment and control over multiple instances in that environment. Members of this role have access to the Yellowbrick Manager Configuration tab, where they may grant the same set of privileges to new users as required. Other users will not have access to this tab and will only see the instance where their accounts were created.
Users who are added to
consumeradminmust have a username that includes the realm (for example,newuser@myvpc.com). Asybdadmin(or another user withconsumeradminprivileges), you can go to Configuration > Administrators > +User. For example: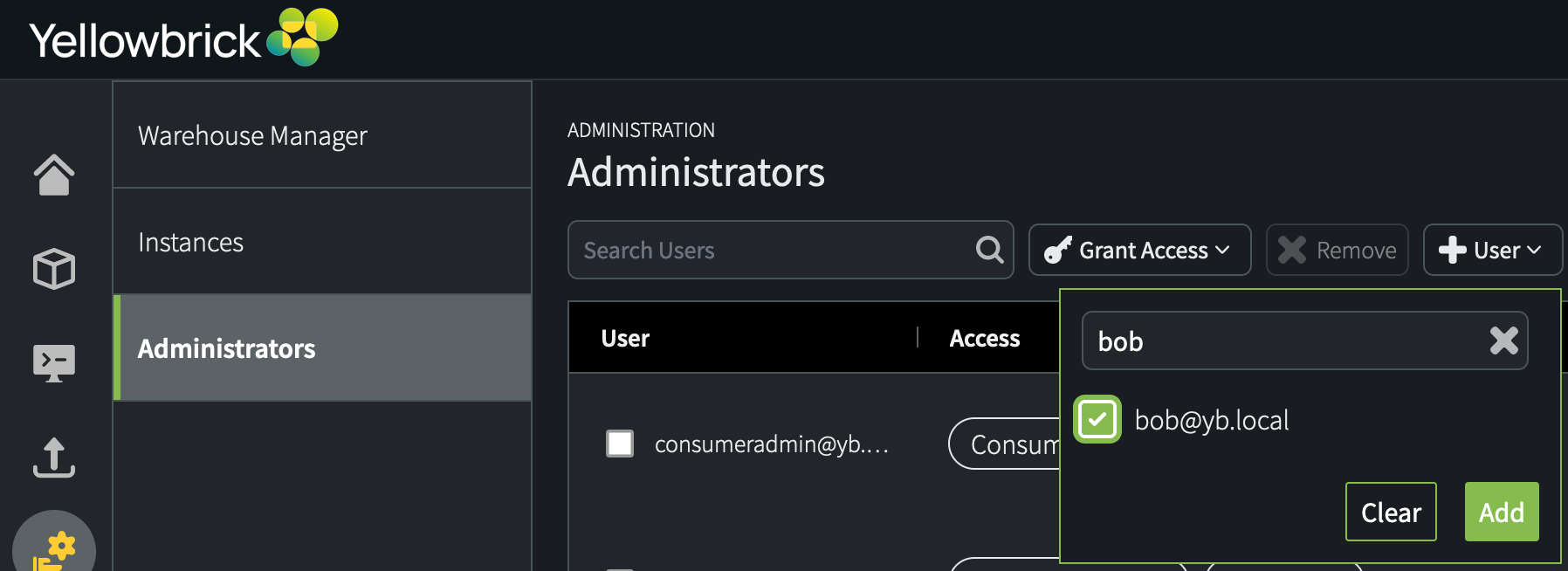
After adding the user, grant access to
consumeradmin.The
ybdadminuser belongs to theconsumeradminrole; however, a new user who is granted membership inconsumeradmindoes not acquire membership in the other admin roles thatybdadminhas.- instanceadmin role
This role grants privileges for database administration: cluster management, database creation, workload management, access control for other users, and so on. A user with membership in this role is effectively a database administrator for a given data warehouse instance. Members of this role may explicitly grant additional users membership in the
instanceadminrole.This role grants membership in other predefined admin roles:
clusteradmin,securityadmin,useradmin,sysadmin(but not theconsumeradminrole).This role does notgive users access to the Yellowbrick Manager Configuration tab or privileges outside the scope of a given instance.
- consumer role
All new users belong to this empty role.
ybdadminhas membership in theconsumerroleWITH ADMIN.- yellowbrick
A
yellowbrickdatabase superuser exists but is not intended for customer use and has no login password.- cdwmdiscsrva
Internal CDWM user, not intended for customer use.
- sys_ybd_* (service accounts)
A number of system-defined no-login service roles exist in the system and are visible in all instances. Do not modify these roles. These role names begin with a
sys_ybd_*prefix. Some of these services run background operations, such as flushing and analyzing tables.
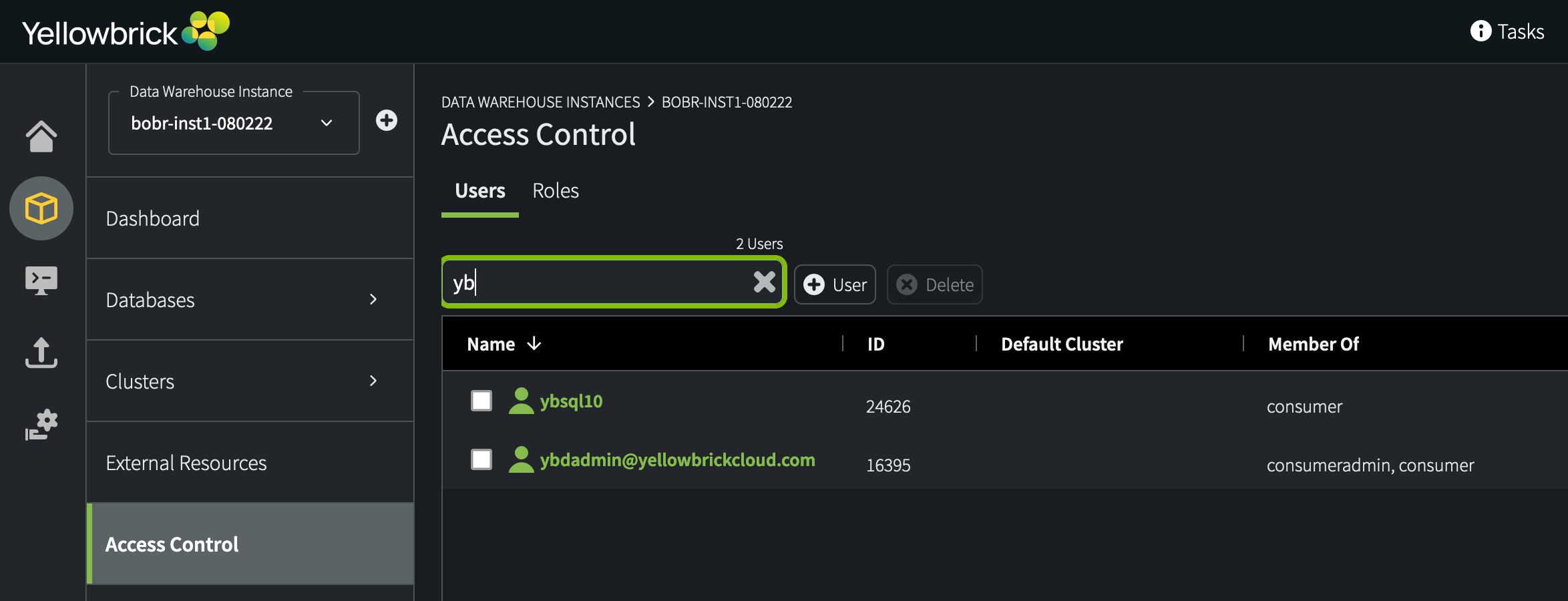
You can create database users and roles by using the Access Control tab in Yellowbrick Manager. Then you can manage these accounts by assigning high-level permissions such as membership in existing roles or ability to create clusters and databases.
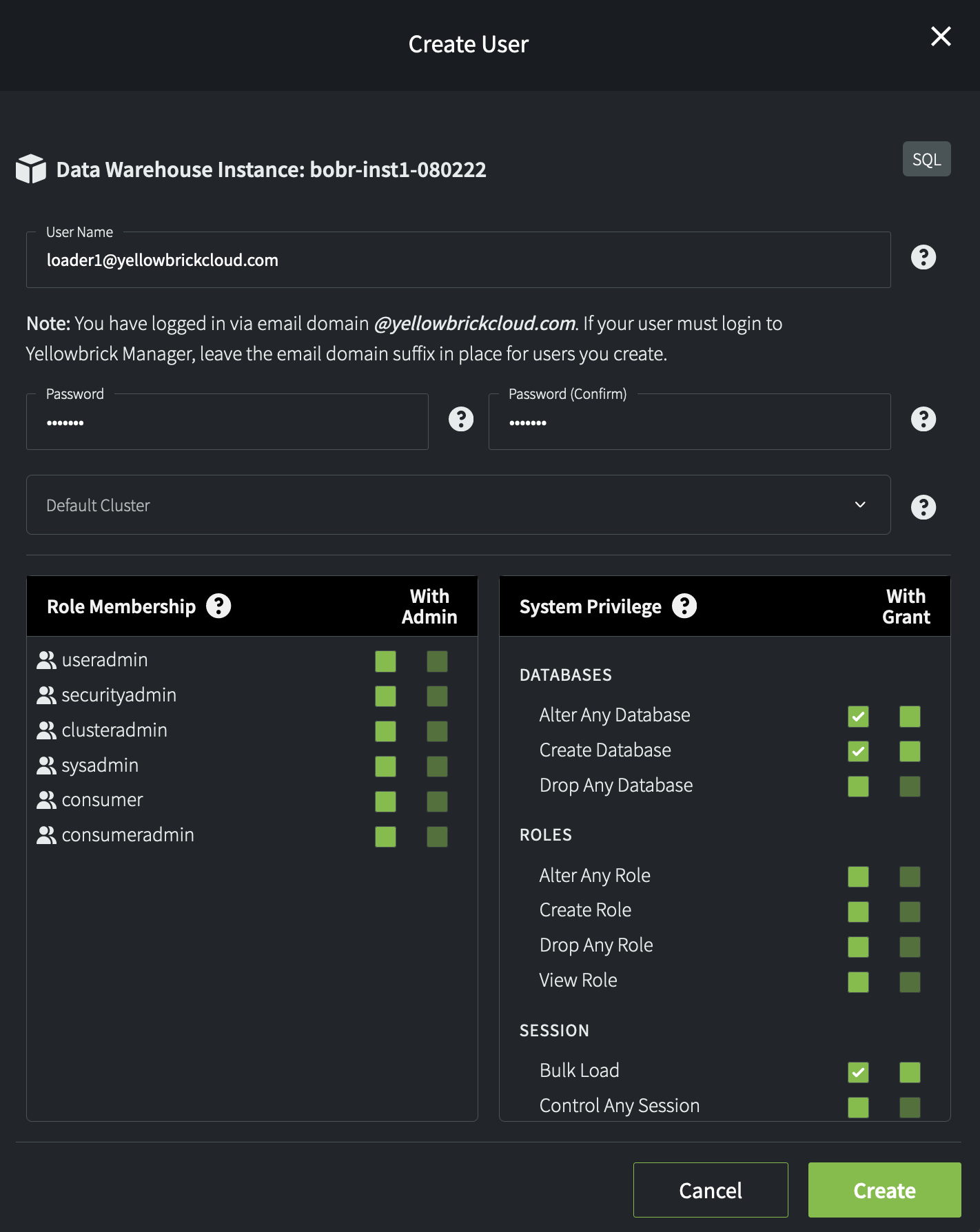
Select Users or Roles, then the + User or + Role icon to get started. In this example, a new user loader1@yellowbrickcloud.com is being created, with general privileges to create and alter databases and run bulk loads.
Users and roles that you create are visible at the instance level. A user created in one instance within a Yellowbrick deployment is not visible when you connect to another instance under the same deployment.
Users who need to log into Yellowbrick Manager (as opposed to users connecting to databases via ybtools or third-party applications) must be created with names that end with the email domain suffix (as specified for the initial login user for your deployment). For example, if your initial login account was ybdadmin@mycloudvpc.com, a new Yellowbrick Manager user could be named ymuser1@mycloudvpc.com or vpcadmin@mycloudvpc.com.
Important: To grant lower-level permissions on specific database objects, go to the Databases tab and drill down to an object, such as a table or view, and manage privileges for the object. You cannot grant these privileges under Access Control. For example, users who run bulk loads need insert privilege on the specific tables being loaded.
See also Managing Database Users and Roles.
Cluster Access
When you create new users and roles, be sure to grant them USAGE ON CLUSTER to at least one cluster. See ON CLUSTER.
Individual users may be assigned a default cluster where their queries always run. See ALTER USER SET DEFAULT_CLUSTER. (The default cluster assignment does not propagate to users from roles.)
Parent topic:Provisioning the Data Warehouse