Appearance
LDAP Synchronization Settings
You must specify the Bind DN and Bind Password settings, unless you are using anonymous bind. To locate users and groups in the target directory, specify the base DN and filter for each type. You can also specify an optional identity attribute that identifies each principal type.
The following settings are specific to synchronization. See LDAP Authentication Settings for descriptions of some common fields. See also LDAP Synchronization: Basic Example and LDAP Synchronization: Examples with Filters.
Be sure to select the Synchronize Users/Groups checkbox:
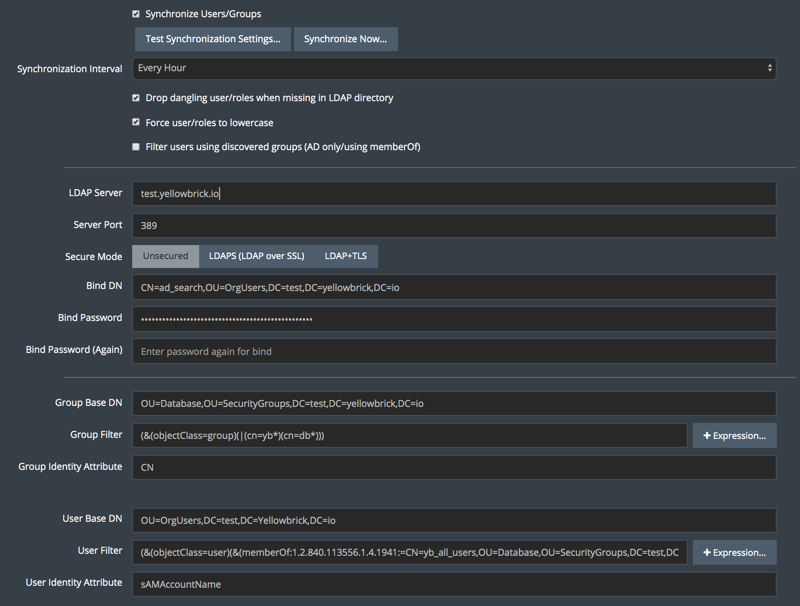
- Synchronization Interval
Select an interval from the dial to specify the frequency of synchronizing LDAP users and groups with database users and roles.
- Drop dangling users/roles when missing in LDAP directory
This option drops users and roles from the Yellowbrick database when they are not found in the LDAP directory. If this option is not selected, LDAP-synchronized users and roles that were added to the database at some point but do not exist in LDAP continue to exist in the database. This option does not drop local users that were created manually with CREATE USER or CREATE ROLE and were not synchronized via LDAP.
In effect, when this option is not selected, synchronization only creates new LDAP roles and users.
Note: When synchronization is enabled and this option is chosen, note the following behavior. If you delete a user from your LDAP directory but the equivalent database user owns objects, you cannot drop the database user. For example, if
testuser1is the owner oftest_databaseand you deletetestuser1in LDAP, Yellowbrick returns an error of the form:Could not drop DB group: testuser1: SQL []; role "testuser1" cannot be dropped because some objects depend on it- Force user/roles to lowercase
This option is generally recommended and forces uppercase or mixed-case LDAP user and role names to all lowercase in the Yellowbrick database. Although LDAP searches are not case-sensitive, Yellowbrick user and role names are. They work the same as other database identifiers in this respect. Names that are not double-quoted are forced to lower case. For example, when Force user/roles to lowercase is used, a user named
ADUserin LDAP is created asaduserin Yellowbrick, avoiding the need for quoted identifiers to correctly handle the mixed-case LDAP username.- Filter users using discovered groups
This option optimizes group filtering for very large LDAP directories. All groups that qualify for the group filter will have all their members searched iteratively, including members of nested groups. This feature works with any LDAP server that supports
memberOffiltering, such Active Directory (AD). For example, the initial LDAP search might return 10,000 groups. To retrieve matched users from those groups, 10,000 subsequent searches would be run, one on each group.- Group Base DN
Enter the base search tree DN for locating LDAP group entries.
- Group Filter
Enter the LDAP filter for locating LDAP group entries. If you leave this field blank, the default filter is
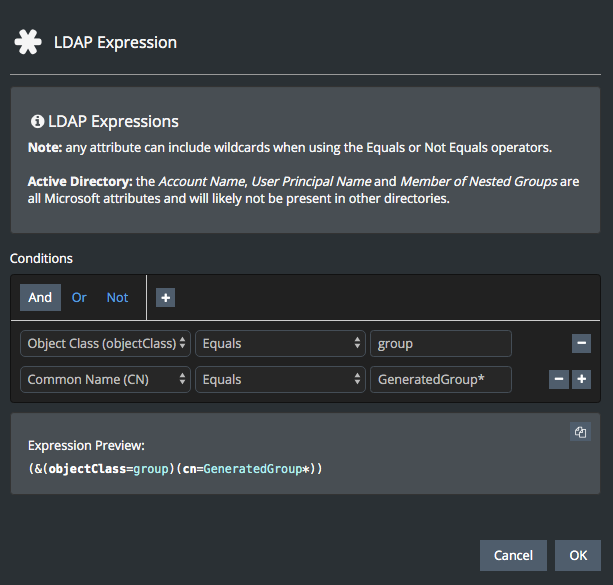
(objectClass=group).Use the Expression Builder to simplify the process of searching through multiple LDAP groups; click the + Expression button to the right of the two filter fields. This interface provides building blocks for the notation that is commonly used in LDAP searches.
- Group Identity Attribute
Enter the LDAP attribute for identifying LDAP group entries. If you leave this field blank, the default attribute is
cn.- User Filter
Enter the LDAP filter for locating LDAP user entries. If you leave this field blank, the default filter is
(objectClass=user).Use the Expression Builder to simplify the process of searching for LDAP users; click the + Expression button to the right of the two filter fields. This interface provides building blocks for the notation that is commonly used in LDAP searches.
- User Base DN
Enter the base search tree DN for locating LDAP user entries.
- User Identity Attribute
Enter the LDAP attribute for identifying LDAP group entries. If you leave this field blank, the default attribute is
cn. For Active Directory setups, consider usingsAMAccountName.
Parent topic:Synchronizing Users and Groups