Appearance
Bind Examples
This section contains LDAP authentication examples for Bind mode. See LDAP Sample Schema for information about the LDAP groups and users associated with these examples.
Open LDAP Example with a Distinguished Name
This example shows the Open LDAP settings for a login that uses a distinguished name (DN) to uniquely identify the user account. To configure LDAP settings for user analyst1 in the OrgUsers organizational unit (OU) at the directory root, set the following prefix and suffix:
- DN Prefix:
uid= - DN Suffix:
,ou=OrgUsers,dc=test,dc=yellowbrick,dc=io
Note: You must include the comma before ou= in the suffix string. The dc entries are the components of the company domain.
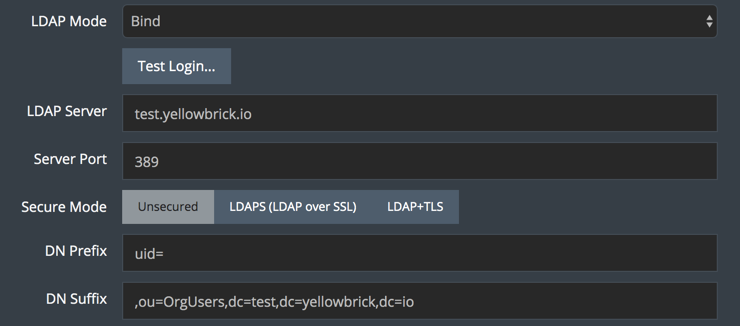
When analyst1 logs into the appliance, the generated LDAP username is submitted to the LDAP server as follows:
uid=analyst1,ou=OrgUsers,dc=test,dc=yellowbrick,dc=ioActive Directory (AD) Example with a Distinguished Name
This example shows the Microsoft Active Directory (AD) settings for a login that uses a distinguished name (DN) to uniquely identify the user account. To configure LDAP settings for user analyst_1 in the OrgUsers organizational unit (OU) at the directory root, set the following prefix and suffix:
- DN Prefix:
cn= - DN Suffix:
,ou=OrgUsers,dc=test,dc=yellowbrick,dc=io
Note: You must include the comma before ou= in the suffix string. The dc entries are the components of the company domain.
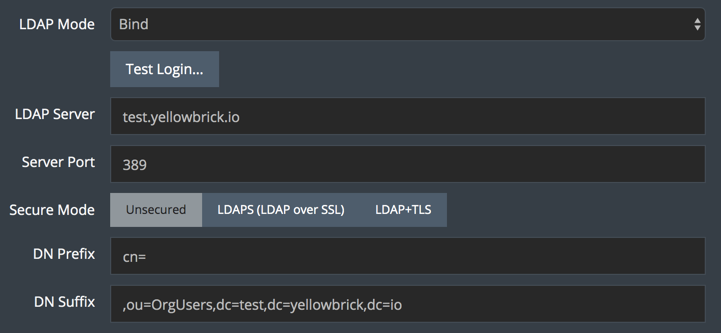
When analyst_1 logs into the appliance, the generated LDAP username is submitted to the LDAP server as follows:
cn=analyst_1,ou=OrgUsers,dc=test,dc=yellowbrick,dc=ioNote that analyst_1 exists only in LDAP. There is no equivalent database user. Therefore, the login is successful, but two warnings are displayed:
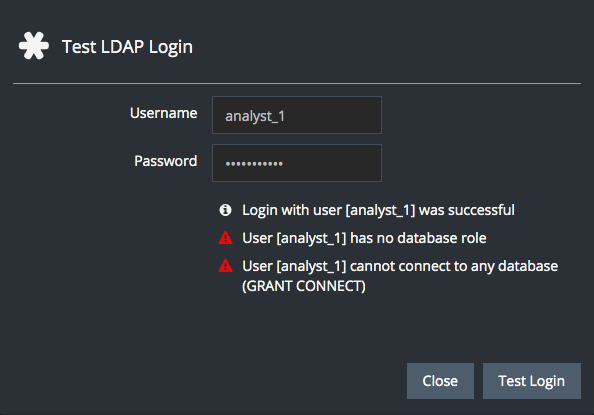
To allow this user to authenticate via LDAP and connect to the Yellowbrick database, you have to create the user in the database (without a local password) and grant the user access to tables and other objects as needed:
premdb=# create user analyst_1;
CREATE ROLE
premdb=# grant select on match to analyst_1;
GRANT
...Now you can retest the LDAP login:
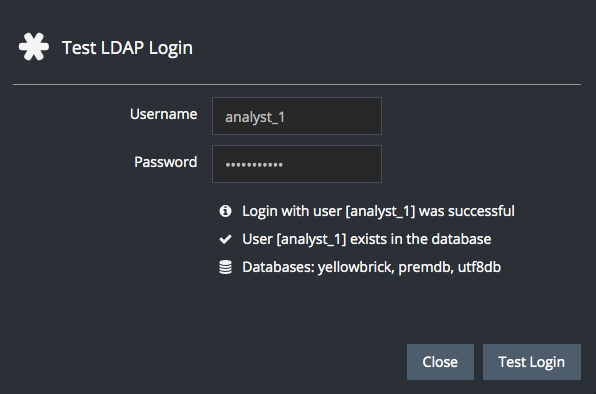
The user can now log in via LDAP, exists as a database user, and can connect to databases.
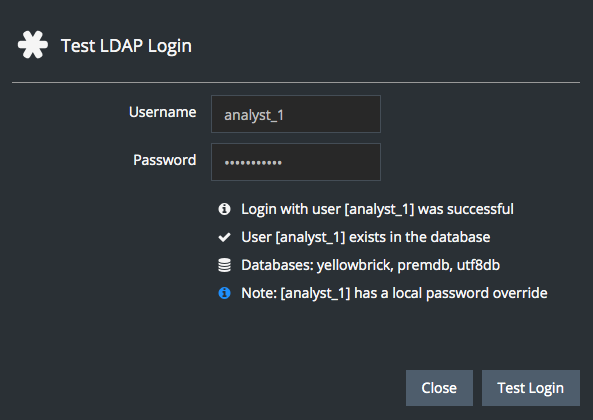
Finally, note what would happen if an administrator gave a local password to this user:
premdb=# alter user analyst_1 password 'local db pswd';
ALTER ROLEThe LDAP login test would still succeed but the user would now be using the local password, not the LDAP password, to authenticate:
Active Directory (AD) Example with a User Principal Name (UPN)
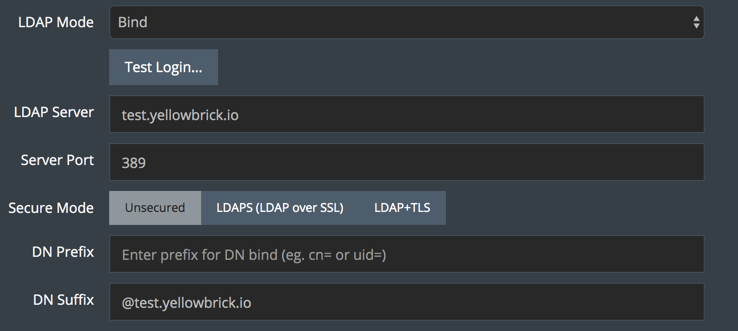
An alternative approach for authentication is to use the user principal name (UPN), which maps exactly to the concatenation of the LDAP sAMAccountName for the user and the @domain string (or email domain).
To configure LDAP settings for user analyst1, set the following prefix and suffix:
- DN Prefix: no prefix
- DN Suffix:
@test.yellowbrick.io
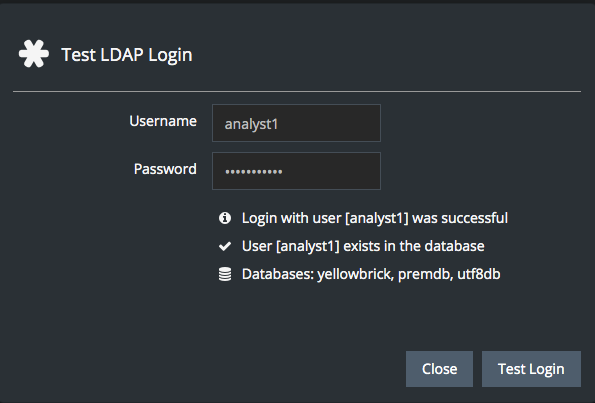
When analyst1 logs into the appliance, the generated LDAP username is submitted to the LDAP server as follows:
analyst1@test.yellowbrick.ioThe LDAP test login will succeed, and if analyst1 exists in the database, the login will return no warnings:
Parent topic:LDAP Authentication