Appearance
Search, then Bind Example
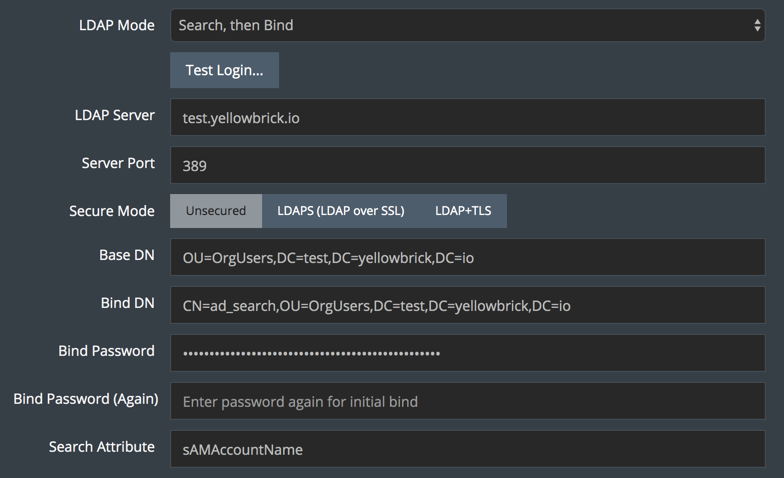
This section contains an LDAP authentication example for Search, then Bind mode with an Active Directory (AD) LDAP server. See LDAP Sample Schema for information about the LDAP groups and users associated with this example.
In this mode, you specify up front a login user whose username and password will be used to search the LDAP directory when other LDAP users attempt to log in with their LDAP usernames and passwords. The Bind DN and Bind Password fields define the initial user. The search starts from a specified base directory (Base DN).
When a login is attempted, the server binds to the LDAP directory with this fixed username and password, then performs a search for the user who is trying to log into the database. The search tries to find an exact match on a specified "search attribute." In this example, the username supplied when the user logs in must match that user's sAMAccountName in the LDAP directory.
The following settings are used in this example:
- Base DN:
ou=OrgUsers,dc=test,dc=yellowbrick,dc=io - Bind DN:
cn=ad_search,ou=OrgUsers,dc=test,dc=yellowbrick,dc=io(wheread_searchis the common name (CN) of the user who will be authorized for the search) - Bind Password: the password for the Bind DN user (specified twice)
- Search Attribute:
sAMAccountName, which is the LDAP attribute that will be used to match login usernames
In this example, analyst1 logs in successfully. In the background, the search for a match on sAMAccountName=analyst1 was conducted after authorizing the initial login for user ad_search.
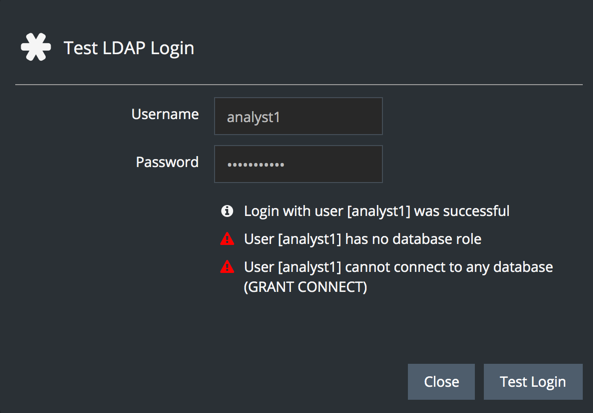
Note that the login was successful, but to allow this user to both authenticate via LDAP and connect to the Yellowbrick database, you have to create the user in the database (without a local password) and grant the user access to tables and other objects as needed:
premdb=# create user analyst1;
CREATE ROLE
premdb=# grant select on match to analyst1;
GRANT
...Then you can retest the LDAP login.
Parent topic:LDAP Authentication